The public key is known to all sending and receiving parties involved in. Asymmetric encryption is inefficient when transferring or encrypting large amounts of data.
Sql Server Best Practices Using Asymmetric Keys To Implement Column Encryption By Alibaba Cloud Medium
For example in an IPSec VPN implementation the data transmission uses a shared secret generated with an asymmetric key algorithm with a symmetric encryption algorithm used for performance.

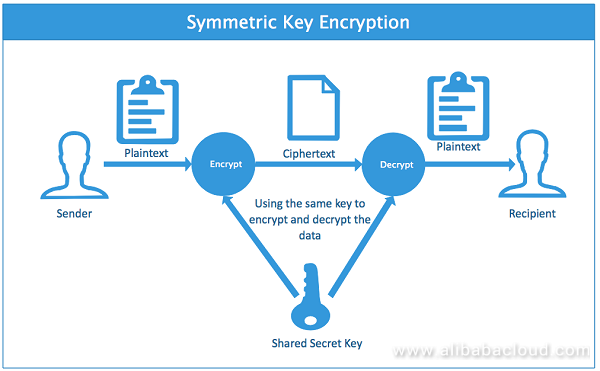
. In symmetric encryption the same key is used for encryption and decryption. Asymmetric key encryption uses two private keys to encrypt and decrypt messages. The opposite is also true.
An encryption method in which two separate keys -- a private key and a public key -- are used to encrypt and decrypt a message. Brea opened an e-mail attachment and it launches a virus. Computer Science questions and answers.
The secret key that is used must be sent over a secure channel to the intended recipientIn the symmetric algorithm data is converted to a form that can only be decrypted by someone who has the secret key. Asymmetric encryption also called asymmetric-key encryption or public-key encryption refers to an encryption method in which two keys are used to encrypt and decrypt a message. An encryption method in which a key is required to encrypt data for storage and to verify its integrity.
An encryption method in which numbers generated by an algorithm from a text string are used to verify the integrity of transmitted messages. Data encrypted with the public key can only be decrypted using the private key. A private key and a public key.
Symmetric key encryption uses only one key both to encrypt and decrypt data. Which statement best. An attackers attempt to decode a cipher by attempting each possible key combination to find the correct one How many encryption key bits are needed to double the number of possible key values that are available.
If a public key encrypts the data the matching private key decrypts the data. The most popular variant SHA-256 produces a 256-bit digest. Engaging in the separation of duties.
The key is pre-configured by the network administrator. Secure Hash Algorithm SHA is considered the strongest hashing algorithm. Asymmetric key encryption uses both a private and public key to encrypt and decrypt messages.
Asymmetric key encryption uses three separate keys for both encryption and decryption. A VPN may use both an asymmetric key and a symmetric encryption algorithm. Both keys are capable of the encryption process but the complementary matched key is required for decryption.
Asymmetric encryption is inefficient when encrypting a large amount of data on a disk or transporting it over a network. Birthday attack What best describes a brute-force attack. AA cryptographic security mechanism that uses two separate sets of public and private keys to encrypt and decrypt data bA cryptographic security mechanism that uses public and private keys to encrypt and decrypt.
Asymmetric key encryption uses a single key for both encryption and decryption. An encryption method in which two separate keys -- a private key and a public key -- are used to encrypt and decrypt a message Which statement best describes asymmetric-key encryption. Which of the following statements best describes asymmetric key encryption.
A public key and a private key. Asymmetric encryption is the strongest hashing algorithm which produces longer and more secure digests than symmetric encryption. Which statement best describes asymmetric-key encryption.
Asymmetric key encryption uses public and private keys. 1Which of the following statements best describes asymmetric key encryption. Asymmetric encryption requires substantially more overhead computing power than symmetric encryption.
Which statement best. Asymmetric algorithms use two keys. Which statement best describes asymmetric-key encryption.
Symmetric encryption is faster and more efficient as compared to asymmetric. Which statement best describes symmetric-key encryption. Asymmetric encryption involves substantially more computing overhead than symmetric encryption.
An encryption method in which a key is required to encrypt data for storage and verify its integrity. The reverse is also true. An encryption method in which numbers generated by an algorithm from a text string are used to verify the integrity of transmitted messages.
If a private key encrypts the data the corresponding public key decrypts. Even after running anti-virus software the damage is extensive and she will have to reformat her hard.

Si110 Asymmetric Public Key Cryptography

0 Comments